CVE-2021-45105 - Multiple eptos Releases - Security Advisory - Apache Log4j2 <= 2.17 did not protect from uncontrolled recursion from self-referential lookups
Summary | CVE-2021-45105 - Apache Log4j2 <=2.17 did not protect from uncontrolled recursion from self-referential lookups. Log4j 1.x is not impacted by this vulnerability. Update Bulletin by 22.12.2021 15:00 |
|---|---|
Advisory Release Date | 21th December 2021 |
Base CVSS Score | 7,5 (AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H) |
Products |
|
Affected Releases | eptos modules - 6.1 eptos Search Engine 2.0 - 2.1 only if logging of api's has been turned on (default off). |
Fixed Releases |
|
CVE ID | |
Issue ID | BASE-1396 |
Further information | https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-45105 |
Summary of Vulnerability
eptos core is using impacted Log4j2 2.16 starting from Release 6.1 and after fix for CVE-2021-44228 Multiple eptos Releases Security Advisory - Apache Log4j2 not protected against attacker controlled LDAP and other JNDI related endpoints
eptos APIs are using spring-boot that has a dependency to log4j-api but by default the log4j2 part is not enabled (reference) - starting from Release 6.0, thus there is no immediate impact.
Software Fixes
eptos 6.0.1 updated to the unaffected release 2.17.0 of Log4j2
eptos 6.1.1 updated to the unaffected release 2.17.0 of Log4j2
eptos email collector 6.1.1 (latest, 2021) updated to the unaffected release 2.17.0 of Log4j2
eptos Search Engine 2.1.1, will be updated to latest 2.17.0 of Log4j2
What you need to do
Paradine recommends that you upgrade to the latest Long Term Support release eptos 6.1.1.
Paradine recommends that you upgrade to the latest Long Term Support release Search Engine 2.1.1.
Please consult your Solution Manager
Mitigation
For mitigation you can
check API's are not having logging turned on
install updated log4j ear in core application and restart the system
eptos 6.0
Release | Program | Change |
|---|---|---|
6.0 | eptos core | install updated log4j ear in core application and restart the system |
6.0 | eptos APIs | Not impacted if logging is disabled (default) Check logging is disabled for microservice API's
|
eptos Email Collector
Release | Program | Change |
|---|---|---|
5.3, 5.4, 5.5, 5.6, 5.7 6.0 | eptos email collector |
Not impacted individually since installed as part of eptos core |
6.1 | eptos email collector | Not impacted if logging is disabled (default) Check logging is disabled for microservice API
|
Kubernetes
example for change in eptos-config map
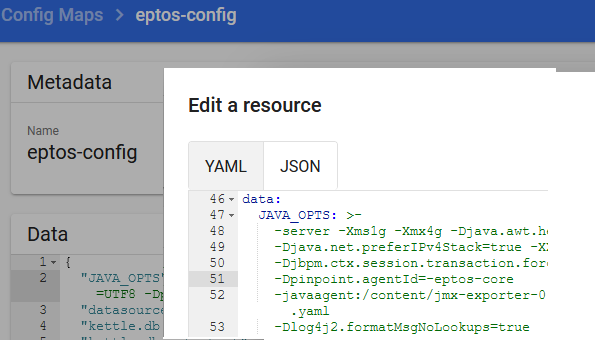
Openshift
Go to Applications→Deployments
Open a deployment plan
Edit as YAML
Update the JAVA_OPTS argument and Save it
Restart Pod

eptos Search Engine
Release | Program | Change |
|---|---|---|
2.0, 2.1 | eptos search engine | Not impacted if logging is disabled (default) Check logging is disabled for microservice API
There might be additionally need for updating the third party SOLR container ! |
Kubernetes
example for change in eptos-config map

Openshift
Go to Applications→Deployments
Open a deployment plan
Edit as YAML
Update the JAVA_OPTS argument and Save it
Restart Pod

See also
Support
If you have questions or concerns regarding this advisory, check support (at) paradine,at and CVE-2021-45105 to your issue description.
